Exemplary Info About How To Prevent Man In The Middle Attack
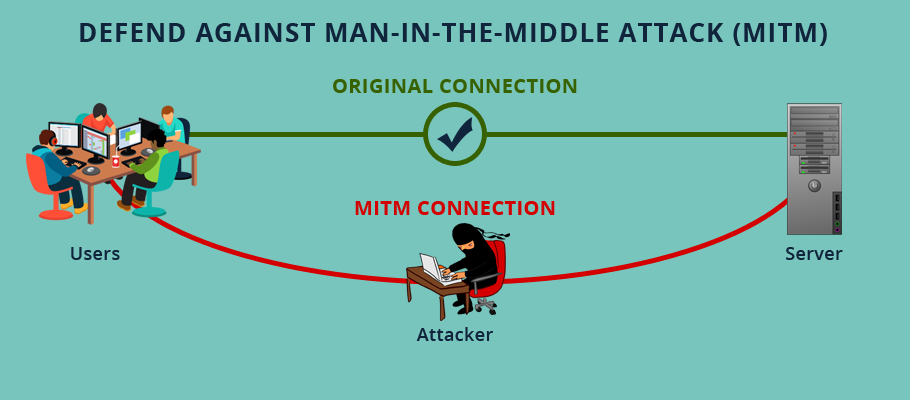
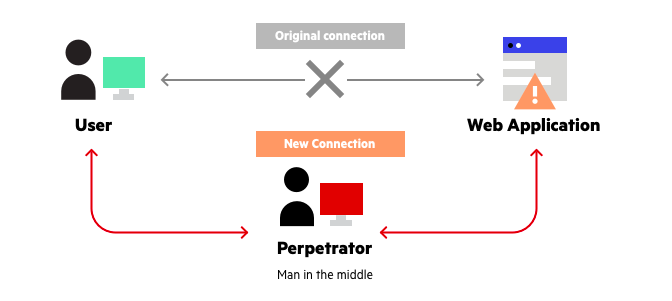
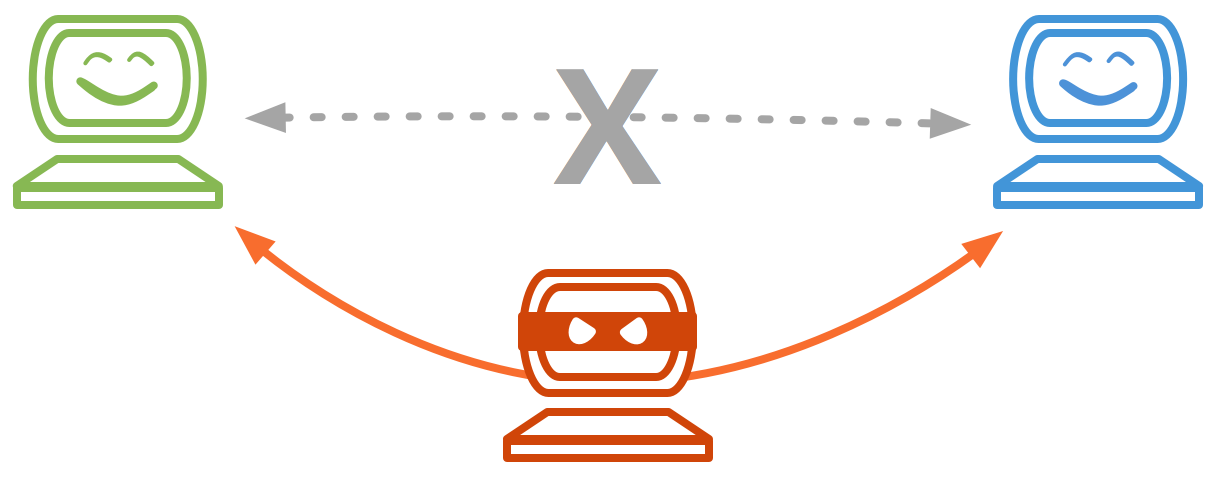
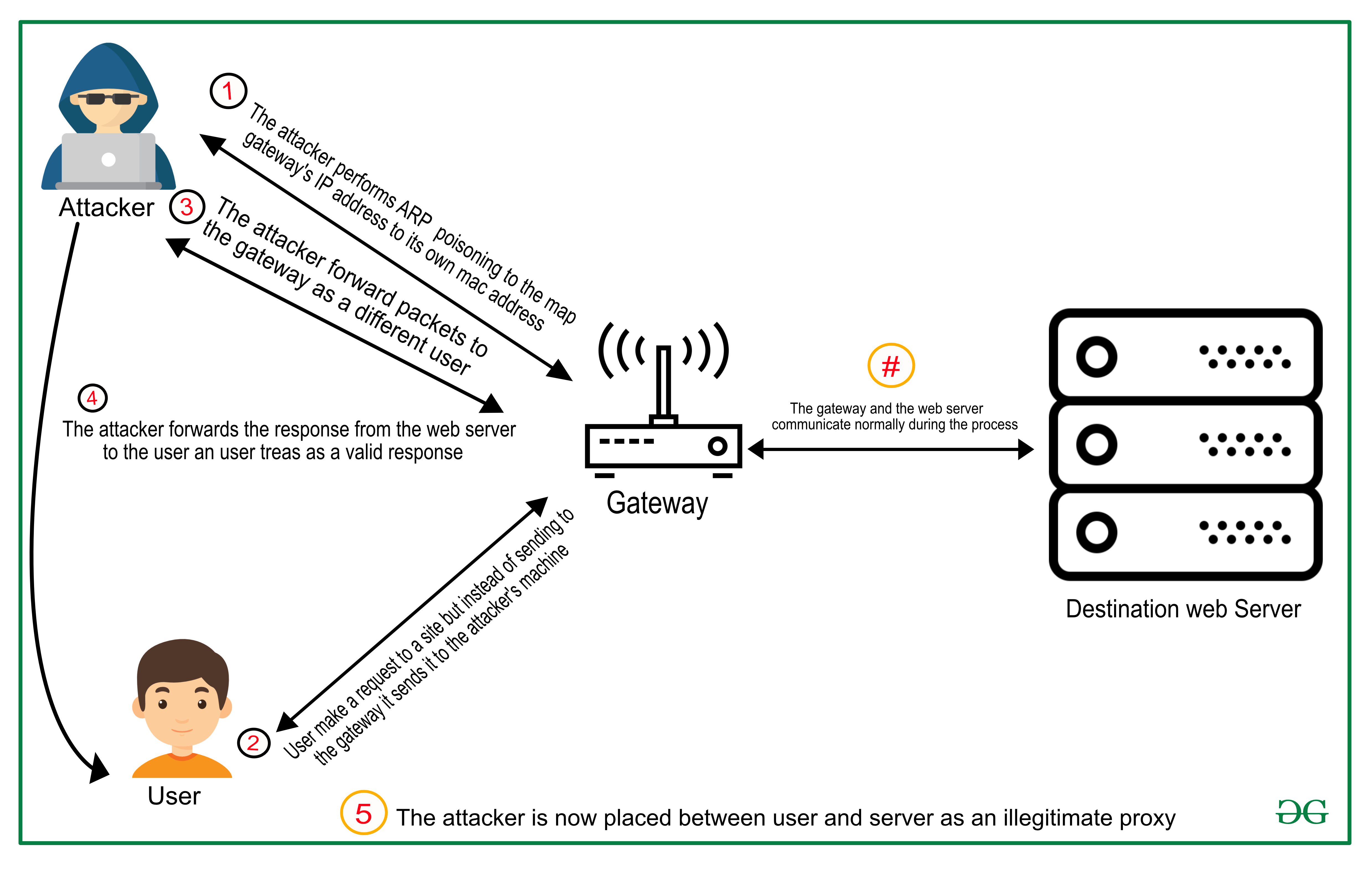
It’s an mitm attack because the criminal spoofs the ip address identification in both directions.
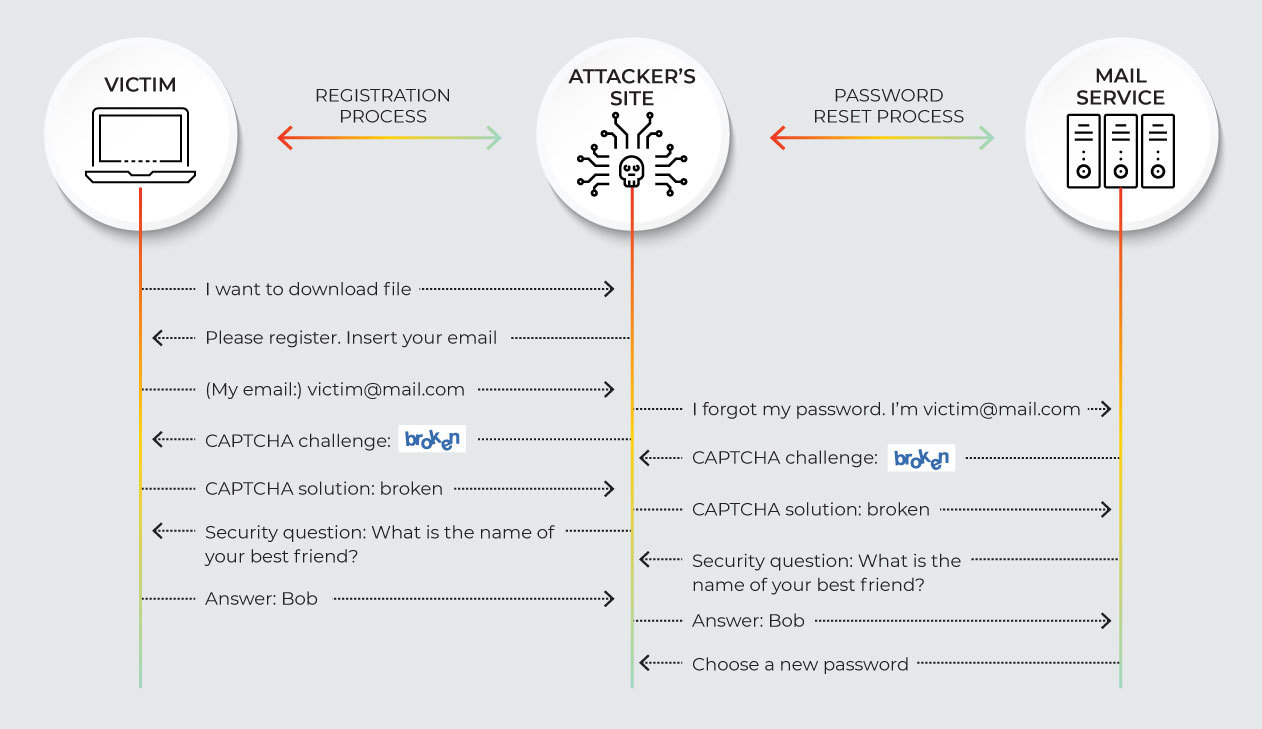
How to prevent man in the middle attack. Most victims are unaware that. As a result, you don’t get your money back and your friend. When you visit a website, your device sends an.
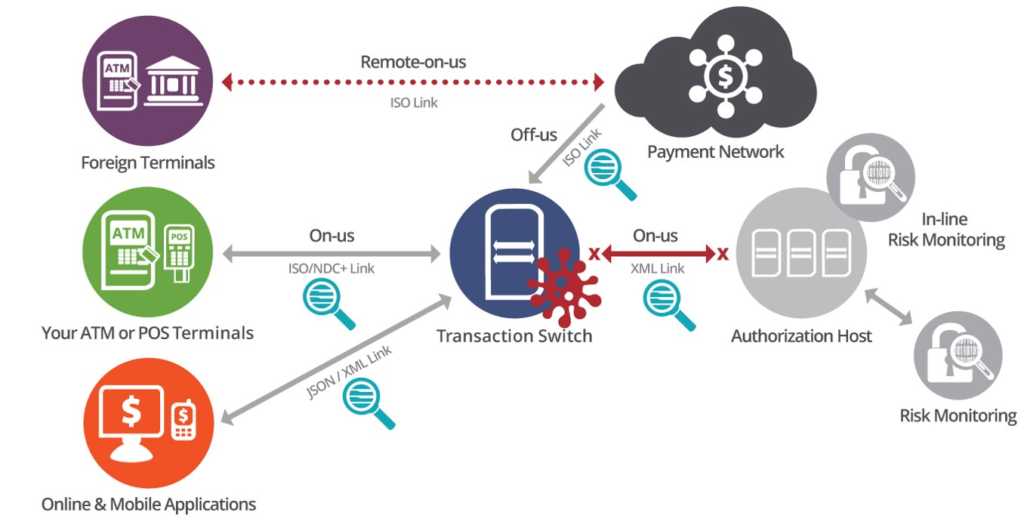
A vpn encrypts data, helping stop attacks from infiltrating. One of the most dangerous and well known threats in cyber security is the man in the middle attack.abbreviated as mitm or mim attack, in this type of attack the attacker. Cybercriminals try to replace a legitimate ip address in dns server records.
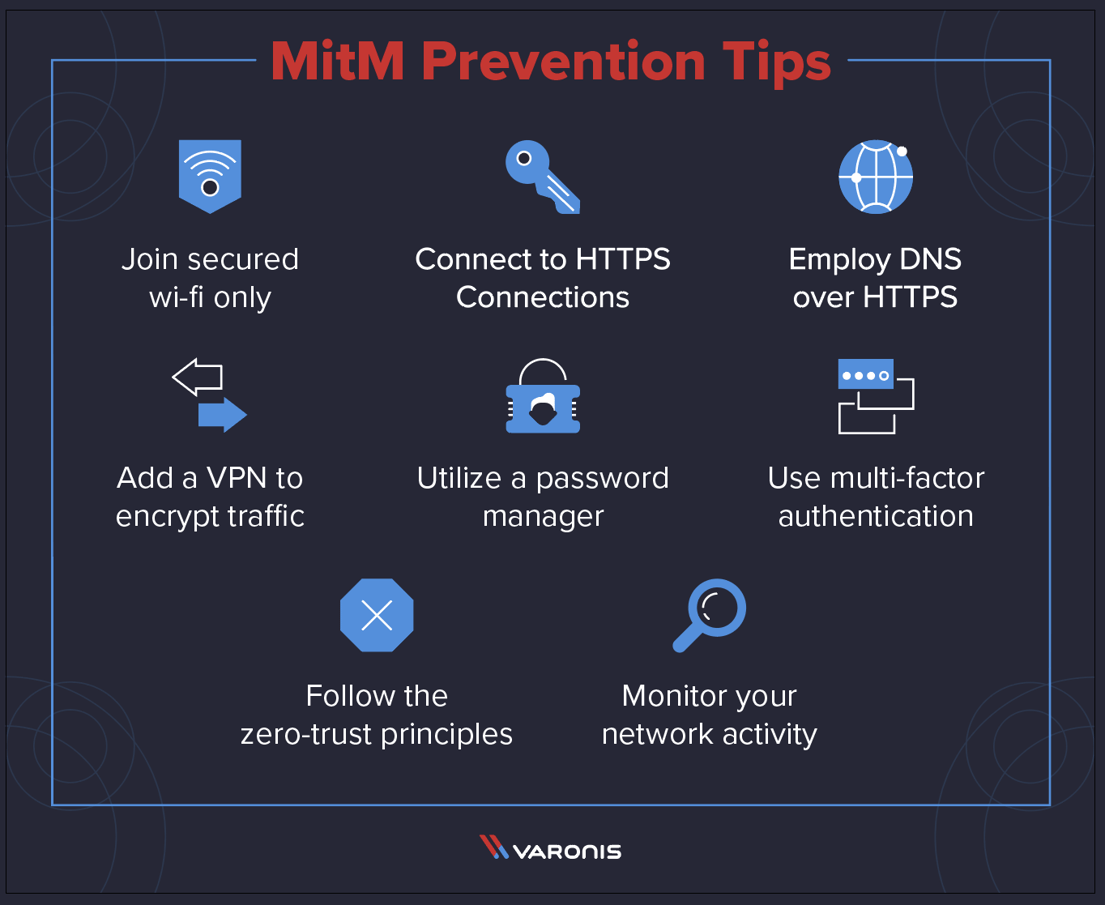
In case yo… see more The victim, the person/entity the victim is trying to communicate with,. To help protect your devices and data from mitm attacks, follow the tips and tricks below:
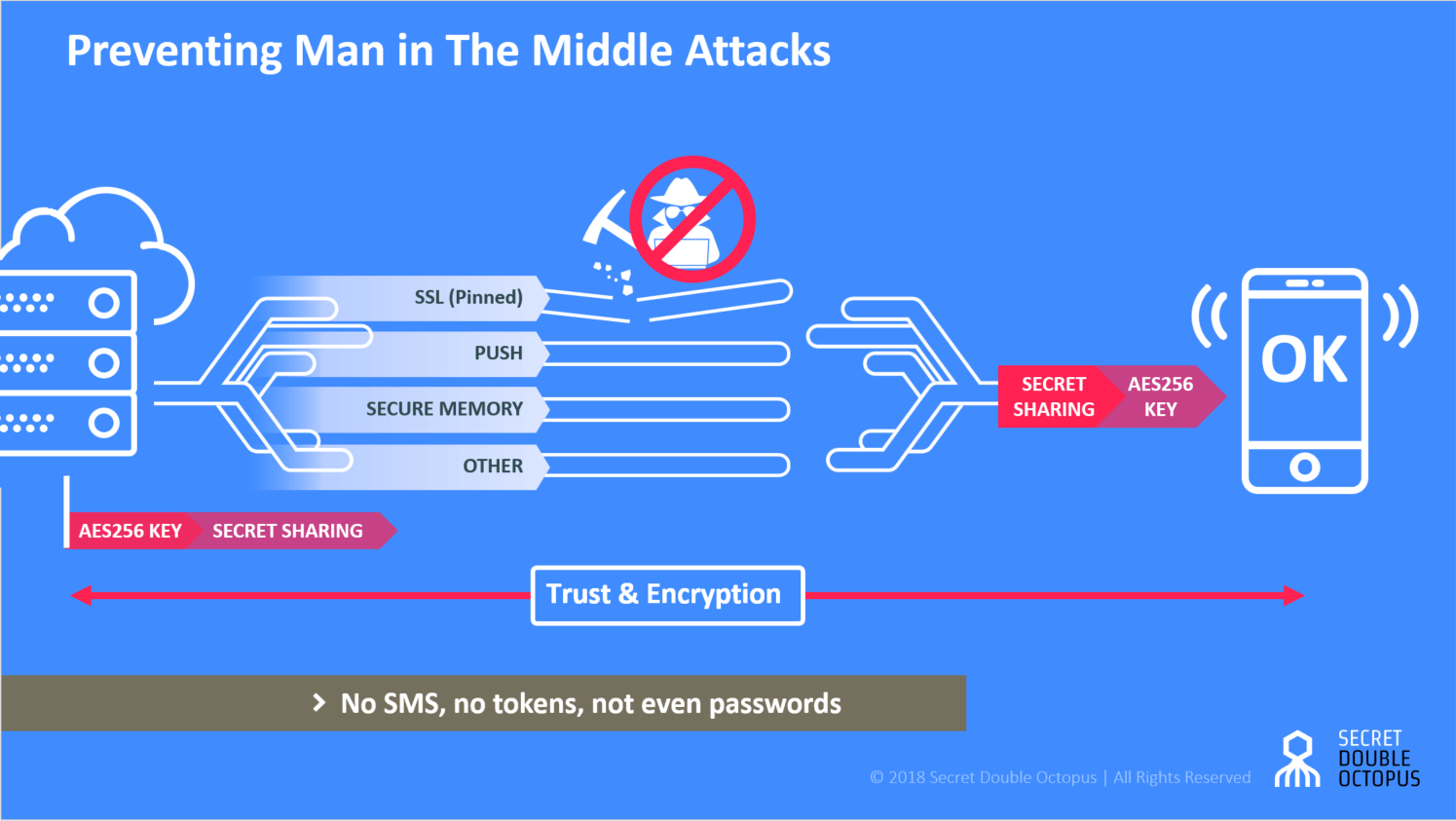
Besides, you can use vpn as a secure tunnel to prevent mitm attack. Here are some proven methods to fortify your mfa: First to the server, which thinks it’s getting a legitimate inbound.
That's accomplished with a combination of security tools, human. It is recommended to use windows xp sp3 or later in order to take benefit of network level. Is there any method to prevent it?
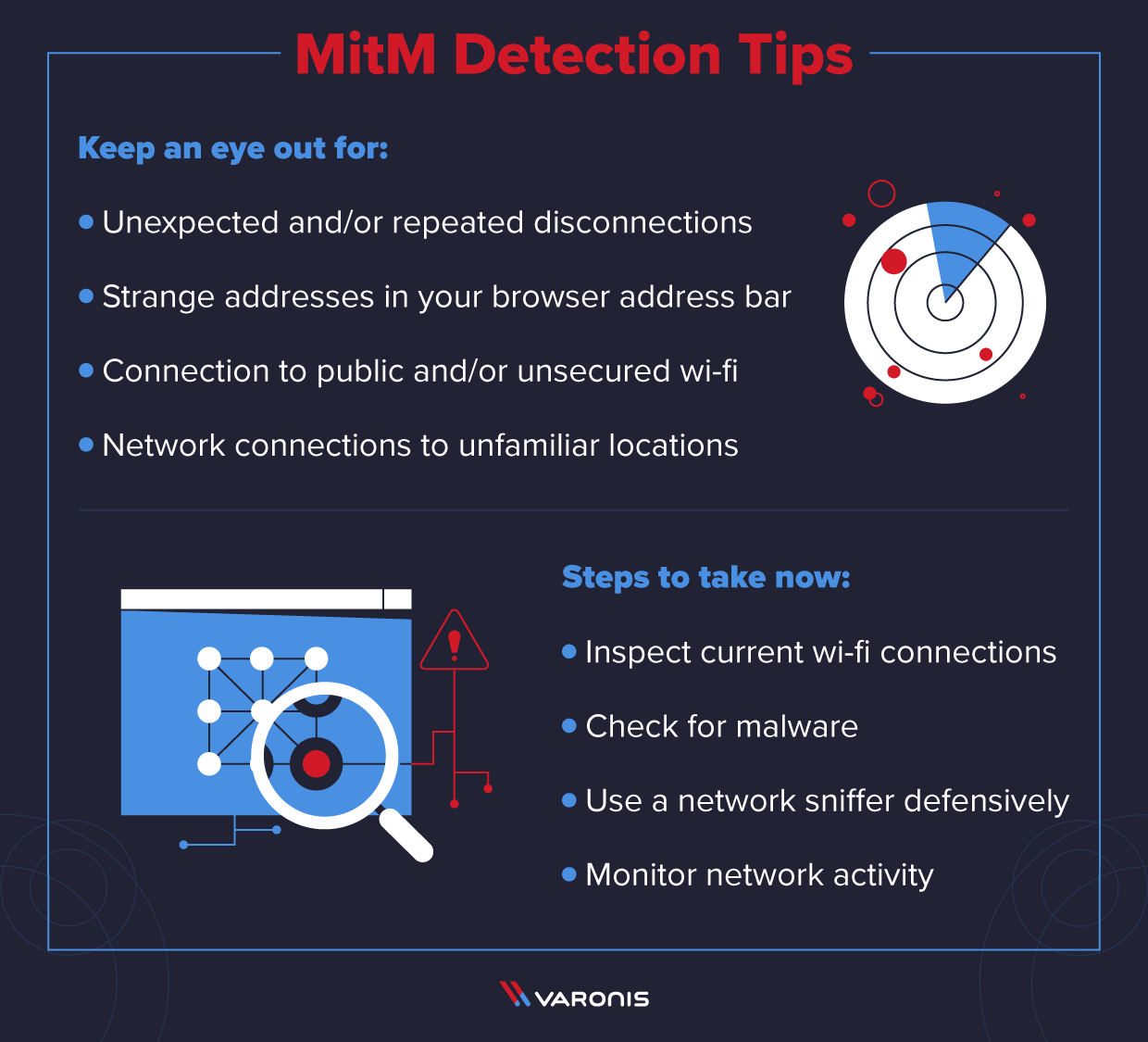
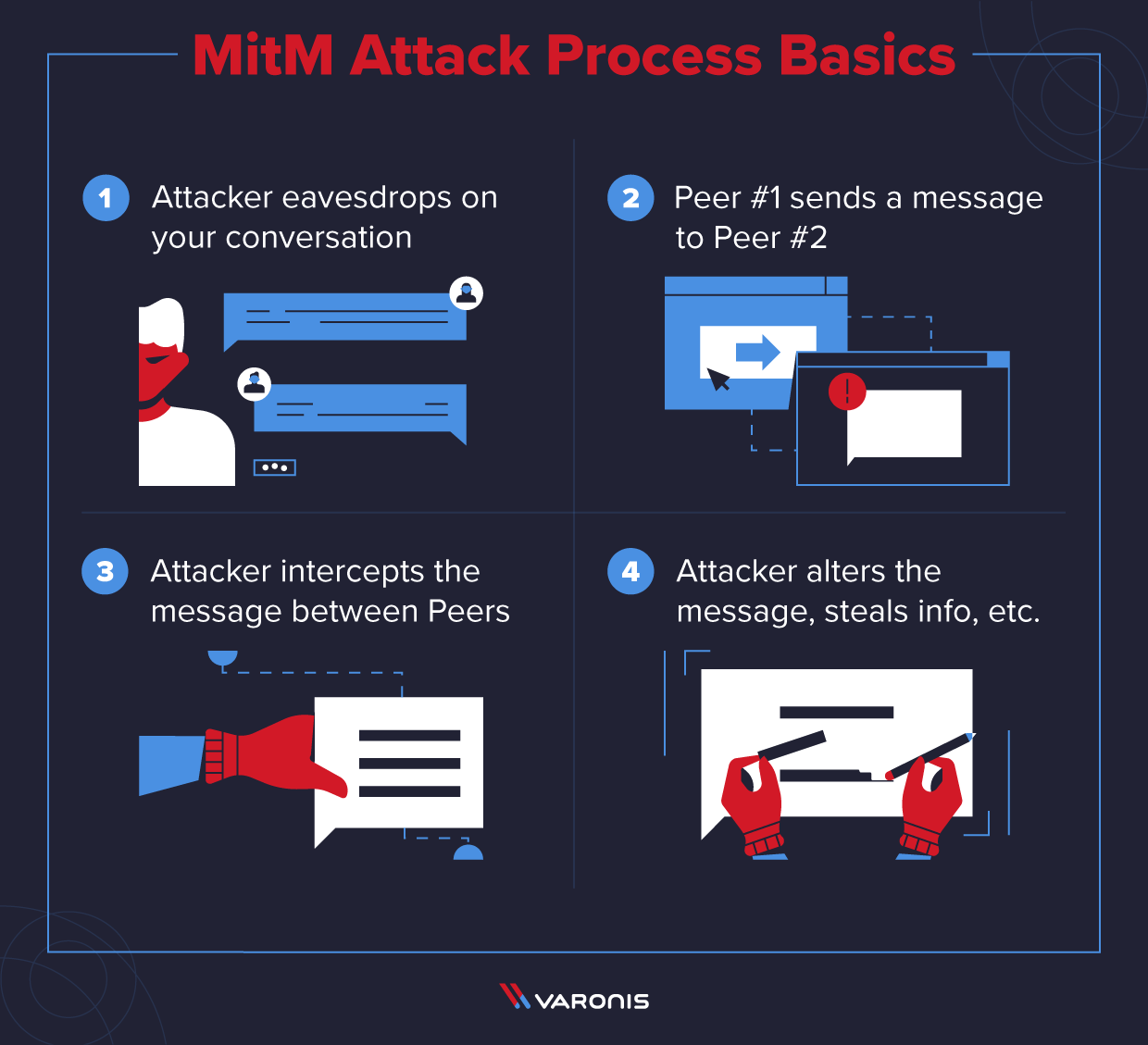
A mitm attack is an interception of communication between two parties for duplicitous reasons. This type of cybercrime is common, potent, and devastating. Keeping networks secure from unwanted external access.




![How To Prevent Man In The Middle Attacks [With Examples] - Firstpoint](https://2mysgjwbwsh23s2tf3tflrh1-wpengine.netdna-ssl.com/wp-content/uploads/2020/03/Image-01-e1585644934847.png)